I have always wanted to create a custom heads up display for my Z. Something along the lines of a tablet running software that talks to my car and displays various information, gauges, etc. in real time. I started searching around and found a few products you can purchase, but none of them seemed to be exactly what I wanted. So then I started looking for ways to do this myself. The first step is figuring out how to talk to the car. OBD2 ports are standard on cars (located under the driver side dash) and offer a way for service techs to hook up and grab information from your car. How much information? A lot. Here’s a list of standard OBD2 information that can be read from a car. But is there more?
It turns out newer cars use a Controller Area Network (CAN) to connect all of the various control modules so they can exchange information. This network only uses two wires, CAN-H and CAN-L, so it greatly reduces wiring. This network is also wired to the standard OBD2 port on pins 6 and 14. This makes the network available to anyone without modifying the car. What’s cool about this is that the information flying around on the CAN is what your car uses to function. So spying on this is like getting a sneak peak behind the scenes of how your car really works. I found a similar project here that got me off to a fast start.
I purchased a CANUSB module and an OBD2-to-serial cable to interface with my laptop. I had to modify the OBD2-to-serial cable because the wiring was slightly off. I just cut it in half and soldered the following wires together:
CAN-L: Serial brown – OBD2 gray
Ground: Serial purple – OBD2 brown
CAN-H: Serial white – OBD2 purple
I left all of the other wires disconnected to keep it simple.
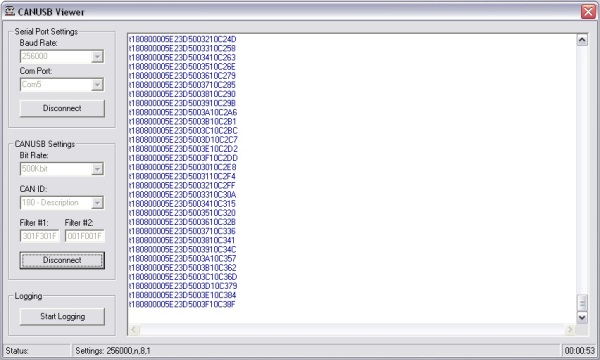
I created a computer program to talk to the CANUSB and log the information that it receives. The screenshot below shows the logger program running and filtering out only messages with ID 180. The messages are shown on the right as they come in.
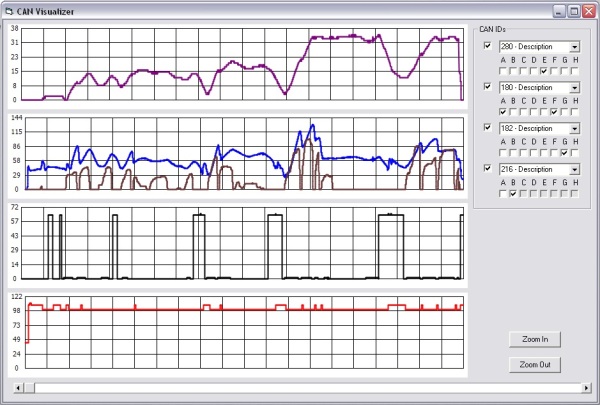
It turns out that the 370Z network only has 30 IDs (or messages) that it uses during normal operation. However, those 30 messages contain a lot of information. Each message may contain up to 8 bytes of data that may represent all sorts of data. One byte may be the gas pedal position, two bytes combined may be the vehicle speed, one byte may be a bitfield that shows the status of 8 different status lights, etc. Sorting through all of this information is daunting, especially since Nissan barely mentions it in their service manual. So I created another program to visualize the data stored by my logging program. Below is screenshot of the program displaying information from a short drive.
Top: vehicle speed, Top-middle: engine RPM and gas pedal position, Bottom-middle: big spikes show brake light status, Bottom: little spikes show clutch pedal status
The above data is completely unfiltered and no calculations can be performed yet. However, it makes sorting through and comparing data much easier. Next I will add the ability to pull the OBD2 standard information along with the data I already capture. This will allow me to compare known information with the data flying around the CAN. I’ll update my progress on this spreadsheet, which shows what I’ve decoded so far. More to come soon.

Pingback: 370Z CAN Bus Proprietary PID's - Nissan 370Z Forum
This is very interesting! I’m trying to learn more about hacking the 370Z myself so your info is really helping out.
Have you done any more since you posted this? 🙂
LikeLike
Yeah, here’s another post I made about finding Nissan’s proprietary PIDs: Nissan 370Z CAN Custom PIDs
LikeLike
Awesome work! Thanks for replying 🙂
LikeLike
Hi, thanks for sharing this work. I am doing quite a bit of work on older Nissan ECUs which have different addresses on the bus. Was hoping you’d be willing to share your program CANUSB and VISUALIZER?
LikeLike
Unfortunately, I lost these files in a hard drive crash and I haven’t worked on it since then. Depending on how old your Nissan is it might not even have a CAN bus.
LikeLike
Disappointed to hear that. I’ve been looking at the ECUs from 2002 thru 2008. I know the source of the CAN signals but most of the IDs changed mid-2008 so unsure about the data in those packets. Thanks for sharing your findings.
LikeLike